APPTROOPS’S DATABASE PENETRATION TEST WILL
HELP YOUR DATABASE STAY PROTECTED

And will ensure that it is properly designed, configured and maintained
Safeguarding database is never an easy task, and very often the attacks that go after the simplest vulnerabilities that are the ones that are most successful. Organizations must continually assess the security of their database in order to reduce attack surfaces. They need to be vigilant about keeping a lookout for default or weak log-in credentials.
APPTROOPS’S DATABASE PENETRATION TEST WILL HELP YOUR DATABASE STAY PROTECTED
Need of Database security
The database is treated in a very important manner and is considered a precious business asset holding sensitive information like customer data, card details, product and pricing data, a record of employees, supplier information, blueprints, project reports, contracts, and intellectual property.
In order to avoid financial or reputational damage it important to protect your data so that it does not fall in the wrong hands
There has been an increased number of incidents where data repositories are targeted
The testing needs to be conducted on regular basis
APPTROOPS’S DATABASE PENETRATION TEST WILL HELP YOUR DATABASE STAY PROTECTED
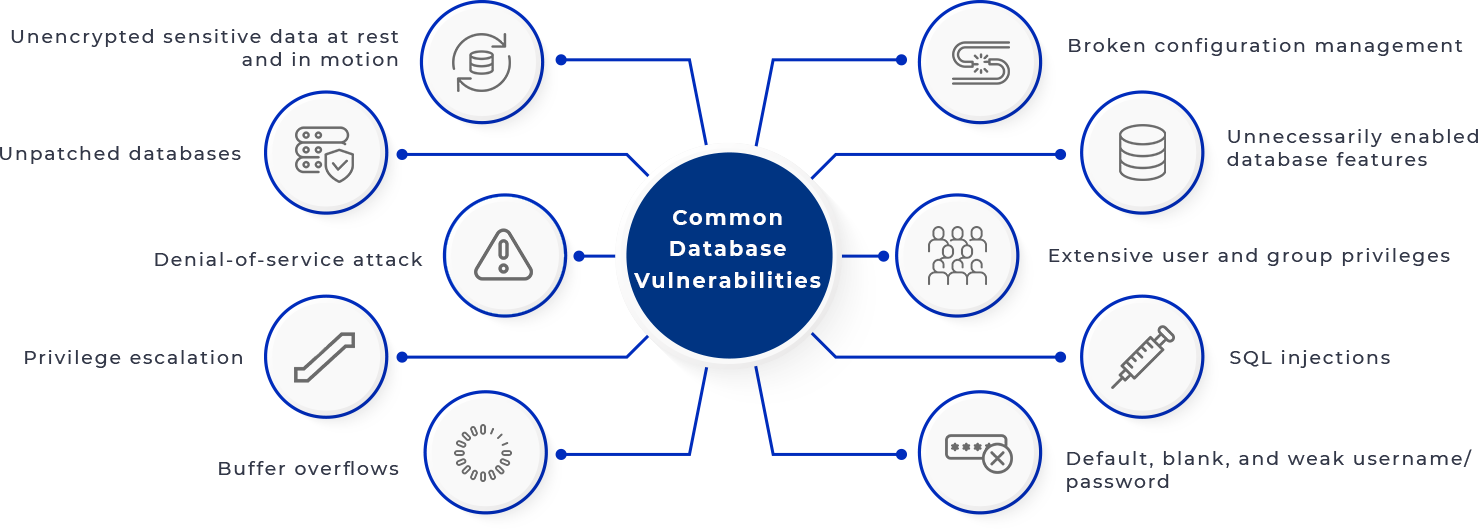
APPTROOPS’S DATABASE PENETRATION TEST WILL HELP YOUR DATABASE STAY PROTECTED
Methodology and Benefits
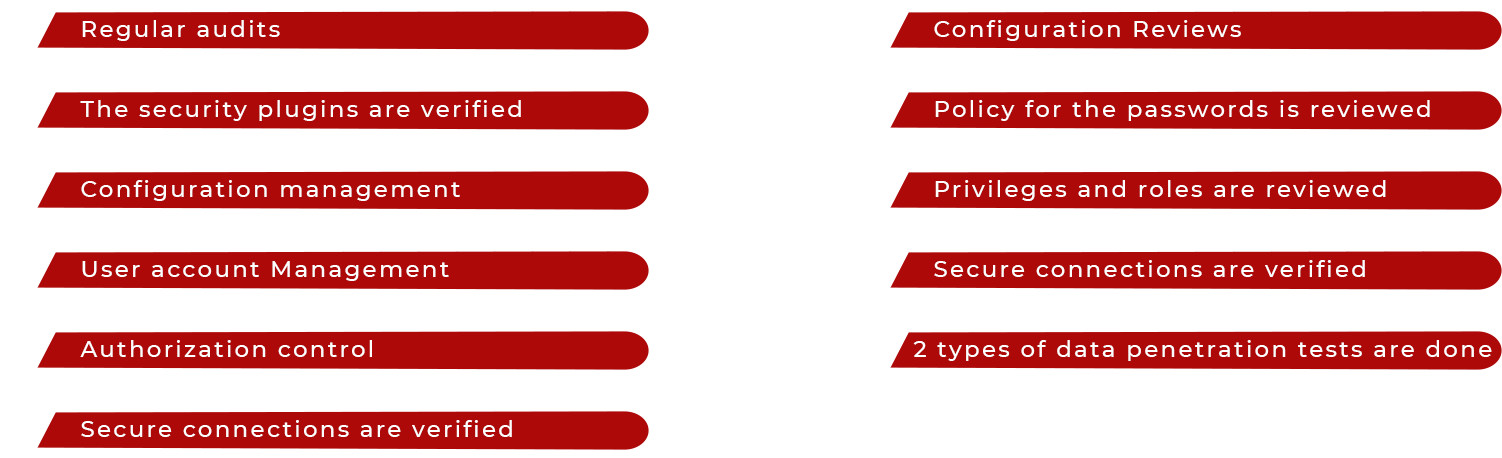
Appsecuri Database Penetration testing is an integral approach, which provides systematic and proactive security to the database