APPTROOPS - CERT
Responds to major incidents, analysing threats, and exchanging critical cybersecurity information with trusted partners around the world.
For any organization facing a cyber attack, the need to understand the situation clearly in order to take control of the breach, avoid panic measures that can ignite the situation and prepare an effective cyber incident response team plan.
Apptroops’s cyber incident response service is made to help businesses manage critical security events. Our experienced experts are skilled at mitigating the destructive effects of cyber-attacks, we investigate how they propagate and provide swift, clear remediation advice is provided.

APPTROOPS – CERT
Functions performed by Apptroops CERT
- An additional in depth and elaborate review of all IT security plans and procedures is done.
- We can promote IT security awareness and manage all audits and drills.
- We can assist you in evaluation of new technologies and techniques prevention and containment.
- We can provide risk management analysis of IT implementations and see how it affects the organization.
- We can investigate new security vulnerabilities and threats and find out the most adequate response.
- We can perform the action of the emergency contact group for the organization.
- We can perform the role of IT emergency system management for all remotely stored system’s critical information.
Key Features of Apptroops CERT
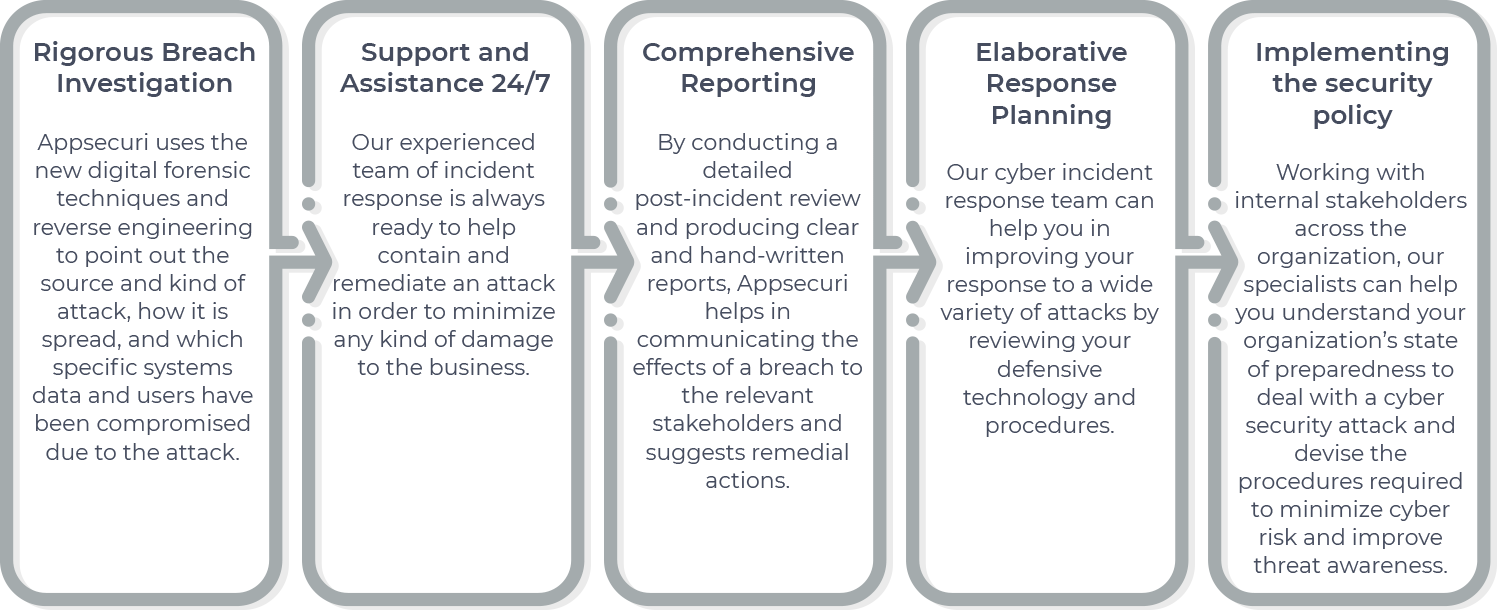
If the breach has happened, Appsecuri helps you to get back your services within hours assets by pinpointing vulnerabilities and misconfigurations