FAST-EVOLVING TECHNOLOGY REQUIRES THE
ORGANIZATIONS TO MATCH PACE WITH IT
Where cloud penetration testing is an example of such evolution
Cloud is a popular data storage solution today, most of the organizations are migrating to cloud. But with convenience comes vulnerability resulting in the increased importance of the Penetration Testing of Cloud-based applications, organizations face unique challenges in protecting their resources over the various models of the Cloud.
Apptroops has experience in testing much larger cloud-based environment including Amazon’s EC2, Rackspace managed cloud, Google cloud platforms and Microsoft’s Azure platform. Security in the cloud needs a well thought of strategy with continuous supervision and surveillance.
FAST-EVOLVING TECHNOLOGY REQUIRES THE ORGANIZATIONS TO MATCH PACE WITH IT
Why is Cloud Service Testing necessary?
This is the cloud generation, with each passing more and more services are migrating to cloud, and being associated with cloud means the need for cloud security testing has increased, apptroops provides cloud-based penetration testing to fulfill all the needs of security vulnerabilities associated with these services.
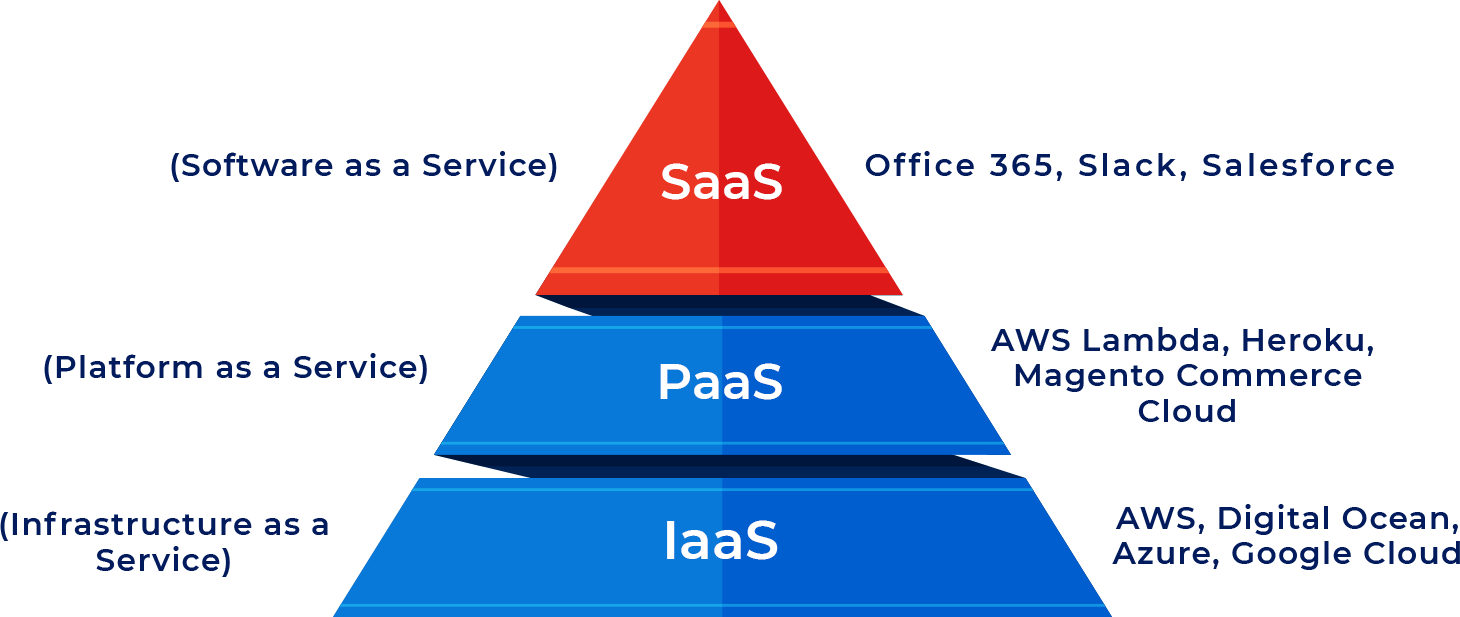
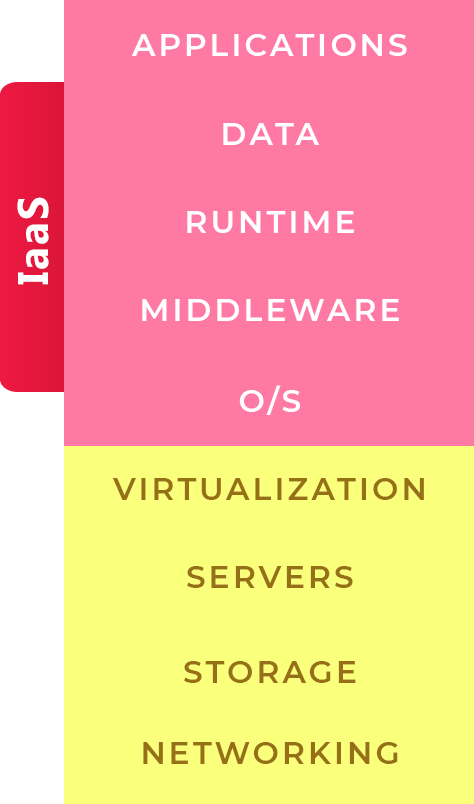
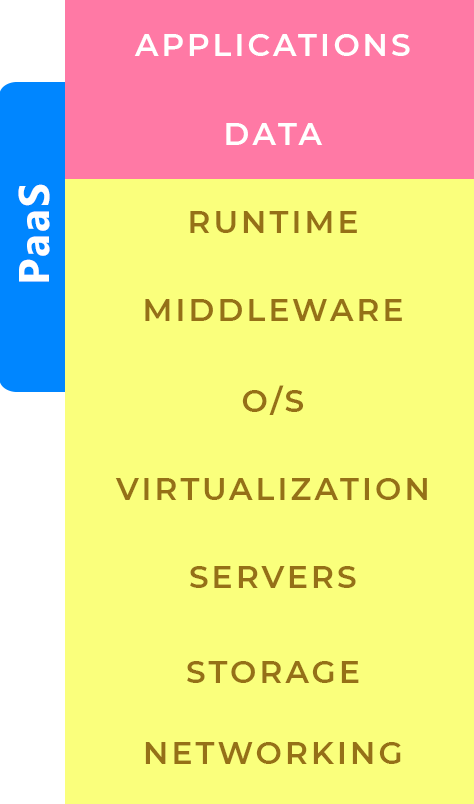
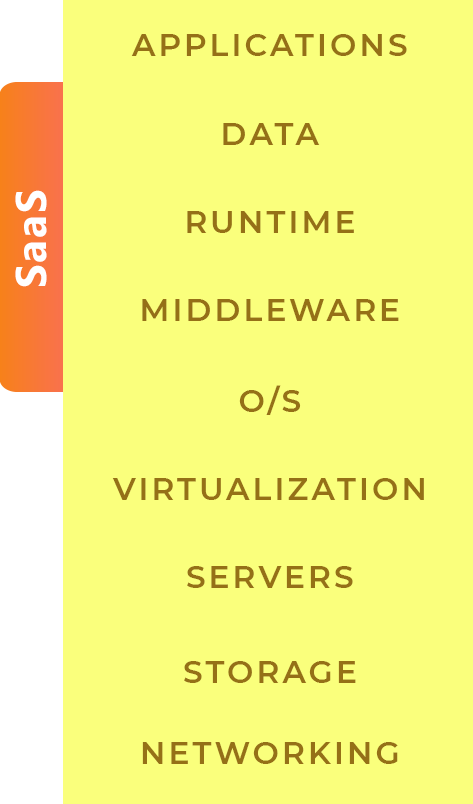
apptroops is proficient in testing and securing all types of environments. Be it Infrastructure as a Service (IaaS), Platform as a Service (PaaS), or Software as a Service (SaaS).
FAST-EVOLVING TECHNOLOGY REQUIRES THE ORGANIZATIONS TO MATCH PACE WITH IT
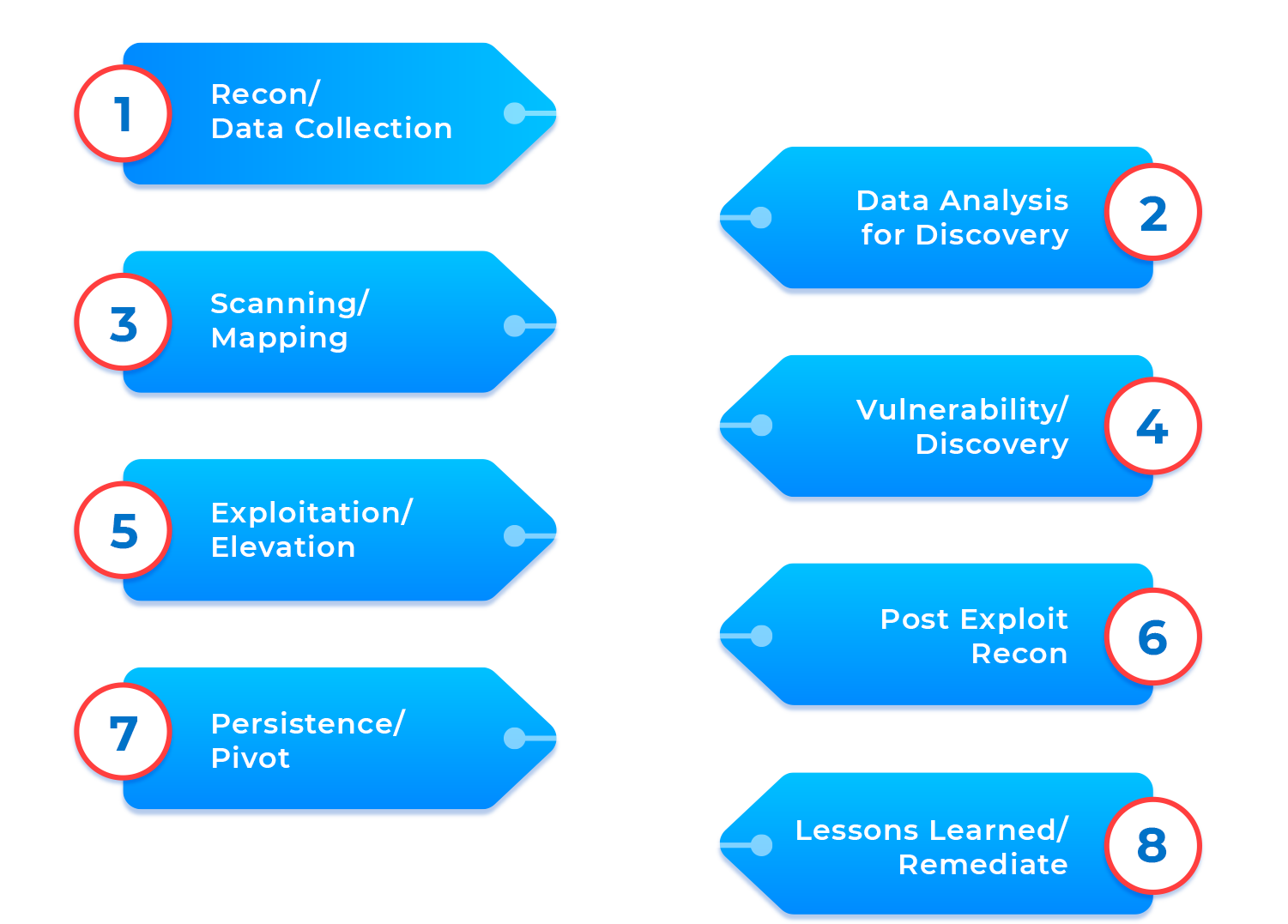
Apptroops Cloud Penetration Testing Methodology
1. Understanding Cloud Provider
Understanding the policies of cloud providers – Almost all public cloud providers have pen testing processes in place. This is often known as the customer support policy for pen testing. This policy specifically defines what activities are permitted and prohibited under cloud penetration testing exercise in their environment.
It is similar to other policies such as network stress testing, DDoS simulation testing. Examples of these pen test rules of engagement (such as Microsoft, AWS, Google or Oracle Cloud Security Testing) or permission policies are available on cloud provider portals.
2. Creating a Pen Test Plan
Understanding the policies of cloud providers – Almost all public cloud providers have pen testing processes in place. This is often known as the customer support policy for pen testing. This policy specifically defines what activities are permitted and prohibited under cloud penetration testing exercise in their environment.
It is similar to other policies such as network stress testing, DDoS simulation testing. Examples of these pen test rules of engagement (such as Microsoft, AWS, Google or Oracle Cloud Security Testing) or permission policies are available on cloud provider portals.
3. Vulnerability Identification Process
Understanding the policies of cloud providers – Almost all public cloud providers have pen testing processes in place. This is often known as the customer support policy for pen testing. This policy specifically defines what activities are permitted and prohibited under cloud penetration testing exercise in their environment.
It is similar to other policies such as network stress testing, DDoS simulation testing. Examples of these pen test rules of engagement (such as Microsoft, AWS, Google or Oracle Cloud Security Testing) or permission policies are available on cloud provider portals.
4. Resource Risk Analysis
Understanding the policies of cloud providers – Almost all public cloud providers have pen testing processes in place. This is often known as the customer support policy for pen testing. This policy specifically defines what activities are permitted and prohibited under cloud penetration testing exercise in their environment.
It is similar to other policies such as network stress testing, DDoS simulation testing. Examples of these pen test rules of engagement (such as Microsoft, AWS, Google or Oracle Cloud Security Testing) or permission policies are available on cloud provider portals.
5. Risk Remediation
Apptroops find vulnerabilities and offer recommendations for better securing the application and the sensitive data it handles assets by pinpointing vulnerabilities and misconfigurations