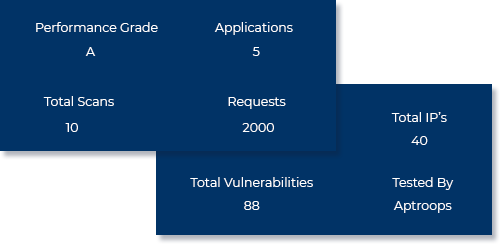
AUTOMATED CRAWLING
For new vulnerabilities and nightly/weekly test and retest will discover the vulnerabilities or zero-days that your other tool didn’t find
Enterprise applications are under threat from various kinds of dangers. The loopholes that can be exploited by hackers are eliminated and the security of the enterprise or the organization is ensured. The old and traditional vulnerability scanners don’t tend to check the critical and high severity vulnerabilities and return a large number of false positives.
Enter the Apptroops Built-In Continuous Scanner

BCS – The Comprehensive Scanner
BCS makes sure that you are secure with its sharp, intensive, precise outputs, scaling a huge number of web applications and with low false positives. BCS delivers application security testing solution that is extremely accurate and a very effective approach for a vulnerability scan.
It involves black box scanning techniques for securities like- Deep Scanning
It involves black box scanning techniques for securities like
- Cross Site Scripting
- SQL injection
- Path Disclosure
- Cross Site Request Forgery
- Command Injection
- Insecure Server Configuration
- Path Traversal
With programmatic scanning of SOAP and REST API services, WAS tests ,IoT services and APIs used by mobile apps and modern mobile architectures.
Wide Coverage
There is a wide coverage where scanning and testing can be done for a wide range of application security vulnerabilities.
Quick Remediation
The remediation is quick with prioritized results and fixed recommendations.
In-Depth, exhaustive application scans at scale
BCS shields you with perfect scans scaling up to thousands of web applications and with low false positives. Whether your network is small involving a single LAN or involves many business units separated by firewalls, continents, all the testing and report generation can be managed and controlled from one location with specific reports being automatically delivered to each business unit.
- Detect OWASP Top 10 risks such as SQL injection, cross-site scripting (XSS), cross-site request forgery (CSRF), and invalidated redirection
- Identifies the open ports and services that are available on each system, such as web and mail servers.
- Scores ranks and identifies high-severity vulnerabilities using the Common Vulnerabilities and Exposures (CVE)
- Identifies servers, appliances, and other devices on the network.
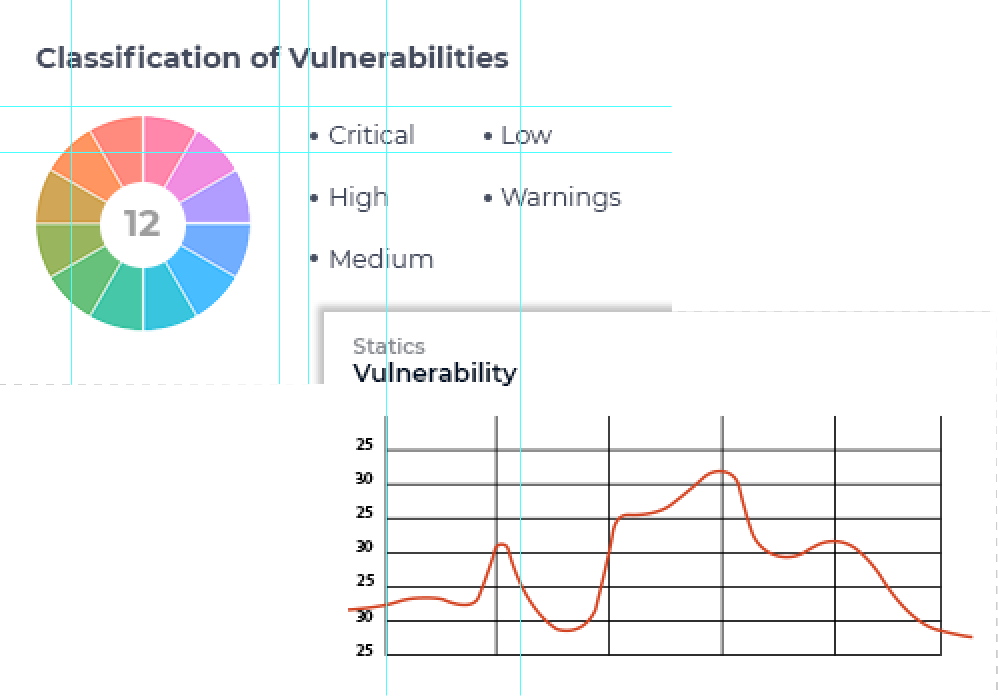
Fast, Accurate and Robust
The scanner is Multithreaded and fast that means it scans thousands of pages at a time without any interruption.
Scans are performed more efficiently
With multi-site scanning and automatic load-balancing of multiple application scans.You can scan extensively and create custom reports showing each audience just the level of detail it needs to see.
Accurate scanning and advanced testing
Of industry’s most advanced SQL injection and cross-site scripting testing with high levels of accuracy.
Support for all major web technologies
Technologies like JavaScript, AJAX, ASP, ASP.NET, PHP, Ruby, JRun and CGI are supported.
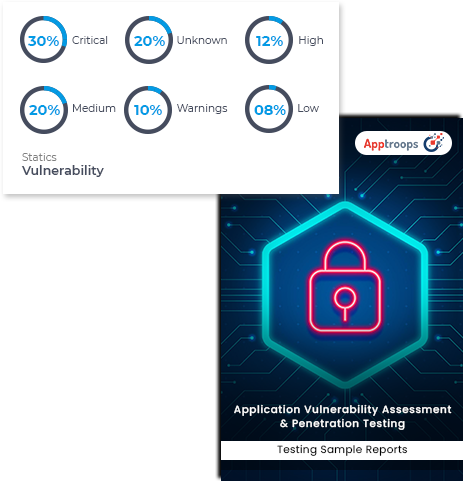
On Demand and Continuous, One-time or subscription to 24/7 application security testing assets by pinpointing vulnerabilities and misconfigurations