A COMPREHENSIVE SURVEY OF YOUR
Network including architecture mapping and a complete network scan
Apptroops Network Penetration Testing constitutes of rigorous testing of the controls, frameworks, and processes designed for the networks related to the system. It penetrates into the key networks of the system with an aim to identify security vulnerabilities and mitigate them much before the attackers try exploiting them.
Our penetration test offers an extremely helpful way to establish a baseline assessment of security as seen from outside the boundaries of the organization’s network.

A COMPREHENSIVE SURVEY OF YOUR
Apptroops Network Testing Process and Services
Our network testing approach is the combination of automating and manual approach. apptroops Network testing simulates network attack activities in order to expose potential entryways to critical or sensitive data. These results uncover the security issues and recommendations and create a compelling event for the entire management team to support a security program.
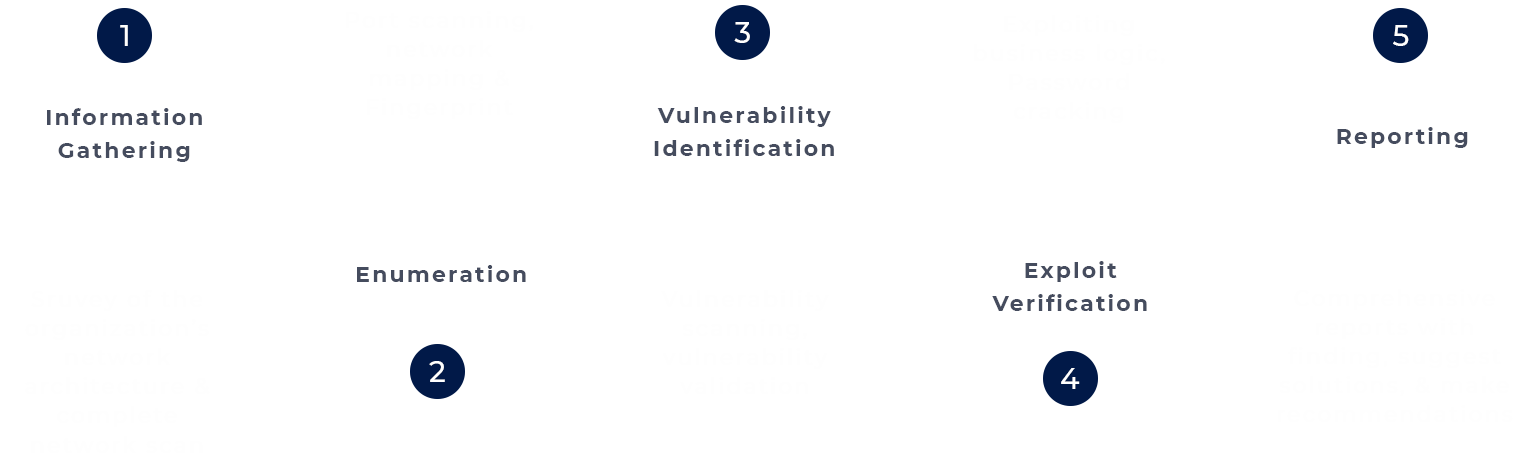
Our aim is to build a vulnerability-free network with apptroops network testing approach and processes. Our methodology lets you identify vulnerabilities and hence ensures the security of your network. We follow a five-phase process that ensures an effective and efficient Security test.
APPTROOPS WSA APPROACH
External Penetration test

APPTROOPS WSA APPROACH
Internal Penetration test
Apptroops find vulnerabilities and offer recommendations for better securing the application and the sensitive data it handles assets by pinpointing vulnerabilities and misconfigurations