Have any questions?
Free: +19177322820

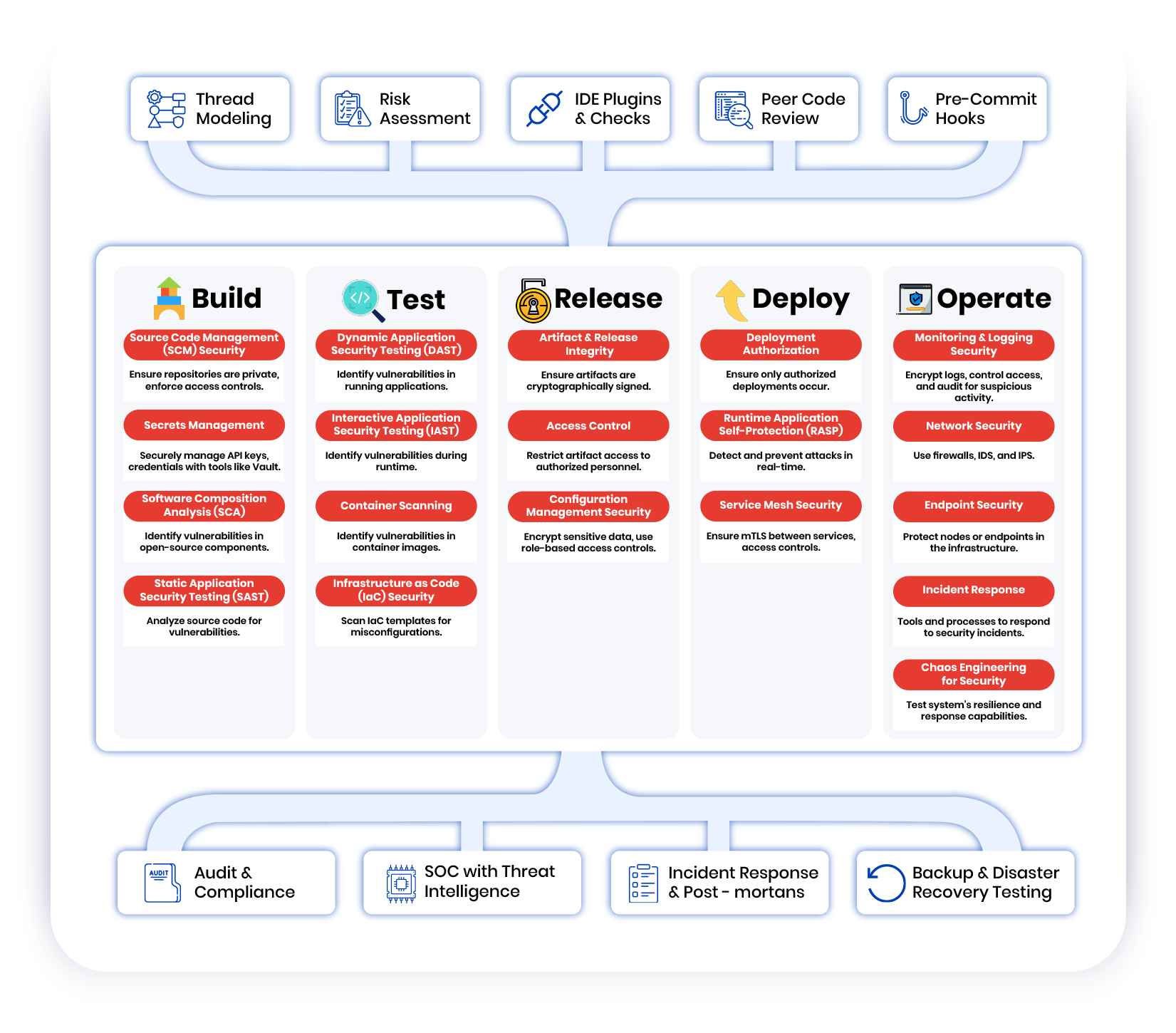
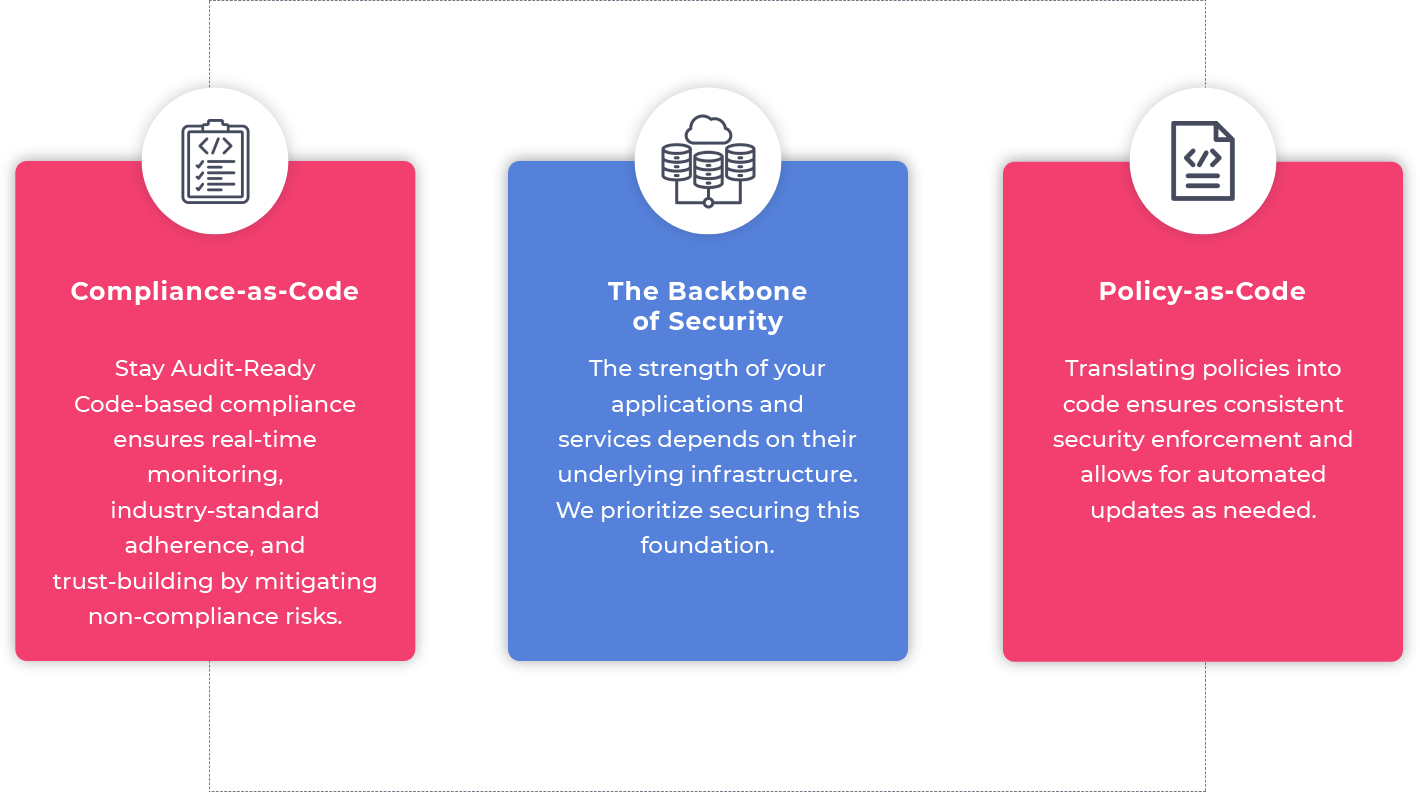
TEAMING
used to hack in organisation

TEAMING
Find Them

TEAMING
and Blue teaming strategies
Request our free 24-Hour penetration test
and get vulnerability report.
- Evaluate skills before any type of engagement with Apptroops.
- Level-1 Testing with manual approach in addition to static/dynamic.
- Get a clear picture of root findings with mitigations in the report.
- 90% of the time we find unknown hidden critical/ high vulnerabilities.
© 2021 Apptroops Technologies Private Limited. All rights reserved